Penetration Testing
Elevate Your Security with Southern Cyber’s Penetration Testing Services. Uncover vulnerabilities, fortify against data breaches, and align with compliance standards.
Our independent verification assures your applications and infrastructure are airtight. Plus, receive actionable remediation guidance to stay ahead in the ever-evolving threat landscape. Protect your business systems and sensitive information effectively with us.

Introduction
Enhancing Security through Penetration Testing. Our Penetration Testing service is a crucial element in fortifying your security strategy. When regularly performed, this ensures the resilience of your applications, websites, infrastructure against compromise, bolstering overall security and compliance efforts. Key benefits include:
- Pinpointing vulnerabilities to safeguard your business systems and sensitive data.
- Dramatically reducing the risk of data breaches.
- Meeting compliance requirements and aligning with security standards.
- Independently verifying the security of your applications and infrastructure.
- Providing practical, clear, and concise remediation recommendations.
Web Application
Internet based applications such as
CMS, e-commerce, financial services customer portals among other things are some of the most common attack vectors.
External Infrastructure
Test and secure your external infrastructure perimeter.
Internal Infrastructure
Understand the blast radius. An internal infrastructure penetration test helps identify what an attacker who has internal access could achieve and how best to mitigate this in the future.
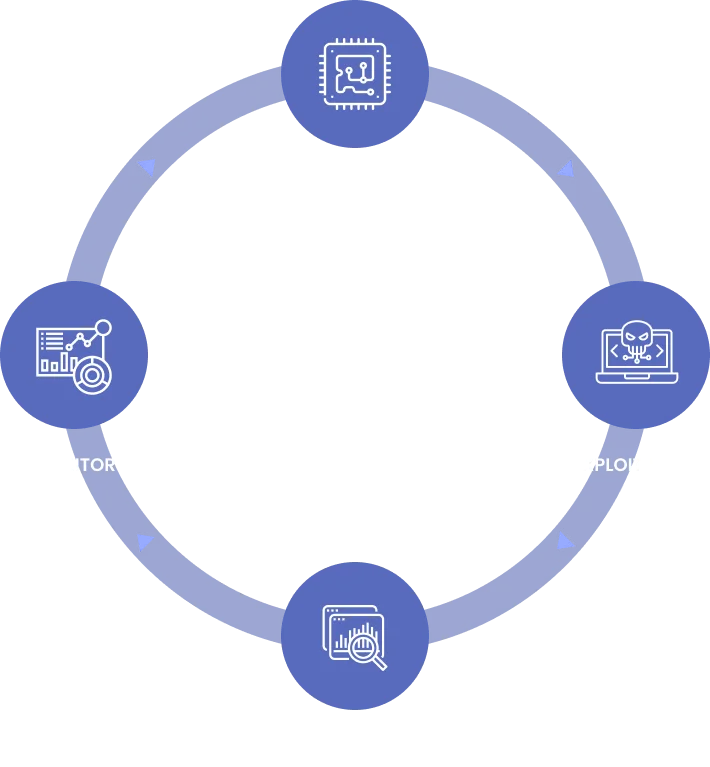
Our approach
Reconnaissance: Identify security vulnerabilities and weaknesses within your applications and infrastructure
Exploitation: Exploit vulnerabilities and weaknesses in your systems to prove compromise
Analysis & Reporting: Detailed report with findings, prioritised risk, and impact along with specific recommendations
Monitor: Monitor the health of your systems over time with regular penetration tests
Contact us
Level 7, 115 King William Street, Adelaide SA 5000