ISO 27001 | Information Security
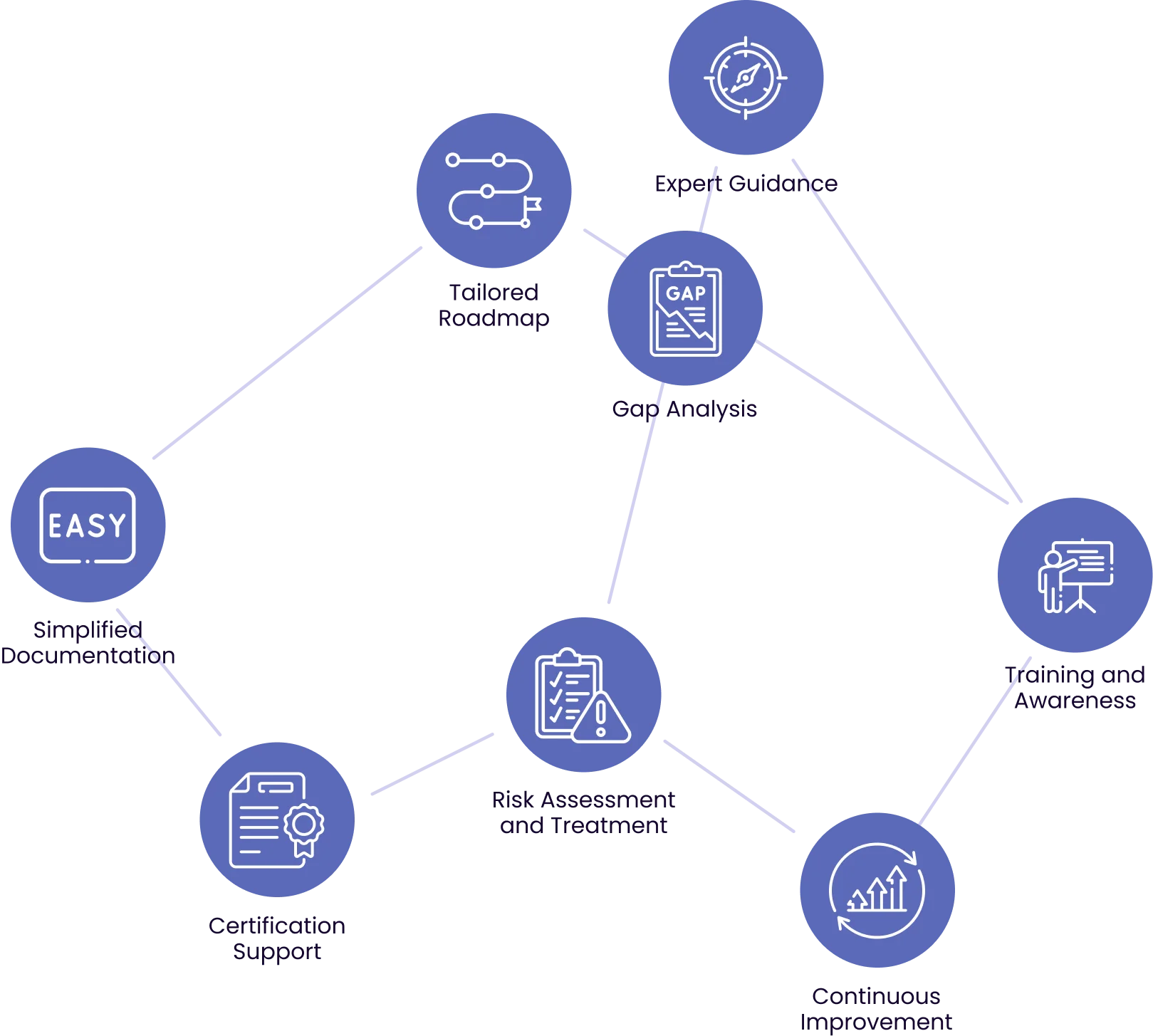
Streamline your path to ISO 27001 compliance effortlessly with our simplified approach, making the complex process easy to understand, implement, and maintain, ensuring robust information security for your organisation.
Southern Cyber have designed a scalable, staged approach that suits businesses of all sizes to ensure you are ready for the extensive process of attaining accreditation. ISO Made Easy…

What is ISO/IEC 27001
The ISO/IEC 27001:2022 standard is a globally recognised framework that provides a systematic approach to managing and securing sensitive information. It helps organisations protect their data by establishing, implementing, and maintaining an Information Security Management System (ISMS). The primary goal of ISO27001:2022 is to safeguard the confidentiality, integrity, and availability of information, ensuring that sensitive data is accessible only to authorised individuals, remains accurate and unaltered, and is available when required.
The standard guides organisations in identifying potential risks to their information assets and implementing appropriate controls to manage and mitigate those risks. It also promotes a culture of continual improvement, meaning organisations regularly review and enhance their security measures to adapt to evolving threats. Through this, the standard aims to maintain a high level of information security and compliance with legal, regulatory, and contractual obligations.
ISO Made Easy
Implementing ISO 27001 can be a comprehensive process, but here are some very basic summations of the steps taken in your journey with Southern Cyber:
Understand the ISO 27001 Standard
Understand the ISO 27001 Standard
We’ll assist you in familiarising yourself with the requirements and principles of ISO 27001. It is a widely recognised international standard for information security management systems (ISMS). You will be provided with an ISO starter pack which details expectations of the journey and the benefits of aligning to the standard.
Define the Scope
Define the Scope
We’ll help your organisation clearly define the scope of it’s information security management system. Identify the assets, processes, and functions within the scope of your implementation.
Perform a Risk Assessment
Perform a Risk Assessment
As always we will conduct a thorough risk assessment to identify and evaluate potential security risks to your organisation. Assess vulnerabilities, threats, and the potential impact of each risk.
Develop security policies and procedures as well as create a set of information security policies and procedures that address the identified risks. These should cover areas such as access control, incident response, data protection, and system maintenance.
Implement Security Controls
Implement Security Controls
Together we will Implement the necessary security controls to mitigate identified risks. This may involve measures such as access control mechanisms, encryption, regular backups, and vulnerability management just to name a few.
Raise Awareness and Provide Training
Raise Awareness and Provide Training
It’s important to ensure that all employees and stakeholders involved in the organisation’s operations understand their roles and responsibilities for information security. Provide training to promote awareness and compliance with security policies.
Monitor and Review
Monitor and Review
Regularly monitor and review the effectiveness of your security controls and processes. Conduct internal audits and assessments to identify any areas that need improvement or corrective actions.
Continual Improvement
Continual Improvement
Implement a process for continual improvement of your organisation’s information security. This involves learning from incidents, addressing vulnerabilities, and updating policies and procedures as needed.
The ISO Journey
Southern Cyber ISO 27001 deliverables for clients
- Project plan.
- Responsibilities.
- Executive management policies.
- Enhanced gap analysis – includes the whole ISO 27001: 2022 Standard text.
- Risk assessment, including a risk database.
- Risk treatment plan.
- Statement of Applicability.
- Management system policies and procedures covering all mandated requirements and numerous others.
- Annex A risk control documents covering all 93 requirements.
- Awareness training material including presentations.
- Competence training material for responsible staff.
- Internal audits and reports.
- Consultancy.
- Integrated management system.
- IT technology report.
ISO Faq’s
How can implementing ISO27001 benefit your organisation?
How can implementing ISO27001 benefit your organisation?
First, implementing an Information Security Management System (ISMS) according to the standard improves your information security and makes it less likely that you will suffer a breach or other type of unwanted cyber incident.
Second, becoming certified proves to interested parties, such as customers, employees, shareholders and suppliers that you are committed to keeping their data secure. This can be a significant marketing advantage where trust and risk are key issues.
Although it’s often perceived to be a technical, IT-centred standard, ISO27001 covers the whole organisation, dedicated to the protection of information in all its forms. It’s not just for software companies and cloud service providers. Many organisations, both small and large, in many different industries, comply with ISO27001, especially as they implement more online processes.
Information and cyber security is an all-enterprise undertaking because all enterprise processes are, in some way or the other, connected via the internet and the world wide web. All enterprises should do all they can to eliminate information security threats. ISO 27001 is the international benchmark for achieving this outcome.
It’s not difficult, nor expensive, nor resource intensive, if done the Southern Cyber way.
What is an Information Security Management System?
What is an Information Security Management System?
An ISMS is a set of process controls that together help an organisation manage their information security by identifying process risks and using the controls to eliminate or reduce them. The management system is simply a set of things you must do to keep on top of your information security. The main components are:
- Information security policy – what are your rules for keeping information secure?
- Objectives – what are you trying to achieve?
- Risk assessment and treatment – what could go wrong and how can you stop it?
- Roles and responsibilities – who does what in your ISMS?
- Competence – does everyone have the skills they need?
- Awareness training – does everyone know about information security?
- Monitoring and measuring – quantifying what’s going on.
- Internal audit – independent checks that it’s all happening as it should.
- Management review – keeping everything under control.
- Continual Improvement – identify and eliminate root causes of nonconformities in operational and management processes to continually improve the system.
- Implement Annex A risk controls – ISO27001 Annex A provides an international benchmarked set of risk controls to eliminate or mitigate the risks identified in the risk assessment process.
- Add in the ISO 27001 mandated written procedures, evidence-backed communication, and continual improvement, and you have a compliant ISMS.
How to become certified?
How to become certified?
It is important to note, there’s no obligation to go for certification to ISO27001 and many organisations choose to simply use the standard as a set of good-practice principles to guide them along the way to running their business in a more secure way. However, many become certified to prove their compliance internally and externally. The main reasons companies certify is because of customer, or interested parties needs, as well as senior management commitment to certify.
When you have your ISMS in place, and it has been operating for a period, and you’re well under way with the Annex A controls, it’s time to book a stage one review with a Registered Certification Body (RCB), also known as an external auditor. This is simply a company that is accredited to carry out audits to the ISO27001 standard and issue certificates.
Stage one is basically a review of how ready you are for the main event, the stage two certification audit. You may pick up a few pointers for improvement (known as nonconformities) at Stage Two but, if these aren’t too serious, your organisation effectively becomes certified and can advertise the fact to anyone with an interest.
But don’t forget the auditor will be coming back every year from now on to reissue certification, so it’s important to keep things running smoothly and continuously improving.
In order to meet the requirements of clause 9.2 of certain ISO standard certification audits (for those in the Annex SL structure), you need to have evidence of a completed internal audit of your management system by a qualified auditor. If you haven’t got an internal auditor within your organisation or resource to train one, then outsourcing your internal audit is the best option.
If this is your first certification audit or you’re recertifying, you’ll need to complete an internal audit of your full management system. If it’s your annual surveillance audit you may only require an audit of certification requirements in accordance with your defined audit schedule.
Whatever your internal audit requirements, Southern Cyber can help! Our qualified lead auditors can provide internal audits and audit reports quickly and effectively.
For clients more than two hours travelling time away from Adelaide, Southern Cyber’s internal audits are conducted remotely.
What does the internal audit consist of?
What does the internal audit consist of?
The audit consists of a combination of document review and discussions with appropriate management and staff. Relevant documented information is reviewed as evidence that the defined processes and procedures are being followed.
After the audit we provide a professionally compiled report that details:
- The agenda and all areas audited within the management system and Statement of Applicability in line with your requested scope.
- Evidence examined and audit trail for all areas of the standard included.
- Positive findings – the things your organisation is doing well.
- Nonconformities – areas found to be non-compliant against the requirements of the ISO standard which you can then use to drive continual improvement.
The report can be used by your organisation to demonstrate to your external certification body that you are meeting the internal audit requirements of the standard.
How much does Certification cost?
How much does Certification cost?
Essential there are 2 main costs, ISO27001 Implementation Costs and the Certification cost.
Certification is achieved through a 2-stage Audit conducted by an external assessment body (Accredited Certification Body), performed approximately 6 weeks apart.
ISO27001 Certification Costs are determined by the time required to audit and take in consideration:
- Complexity and risk
- Industry
- Number of Sites
- Staff numbers
A small business with a single location operating in the service industry may only need a couple of days of auditing to become certified. In contrast, a large multi-site manufacturing stie could take weeks to audit.
Why trust Southern Cyber to implement your ISO 27001 ISMS?
Why trust Southern Cyber to implement your ISO 27001 ISMS?
At Southern Cyber, we bring unparalleled expertise and dedication to implementing ISO27001 Information Security Management Systems (ISMS) across a diverse range of industries. Our team has successfully delivered robust security solutions to clients in sectors such as finance, healthcare, manufacturing, and more, ensuring their information assets are protected to the highest standards.
We pride ourselves on industry-leading turnaround times, allowing you to achieve compliance and enhance your security posture swiftly and efficiently. Our comprehensive approach, tailored to your specific needs, ensures a smooth implementation process with minimal disruption to your business operations.
Additionally, our collaborative compliance platform seamlessly integrates into this process, providing real-time visibility and management of your compliance status. This innovative tool facilitates communication, tracks progress, and ensures that all aspects of your ISMS are aligned with ISO 27001 requirements which also assists in your ongoing surveillance audits.
With a proven track record of excellence and a commitment to staying at the forefront of industry developments, Southern Cyber is your trusted partner for ISO27001 ISMS implementation.
Contact us
Level 7, 115 King William Street, Adelaide SA 5000